Authonet 2 factor authentication with Zero Trust Network Access

IT Service Providers Part 3 - The Authonet ZTNA cybersecurity gateway in use.Подробнее

IT Service Providers Part 2 - Configuring the Authonet ZTNA product to protect the business network.Подробнее

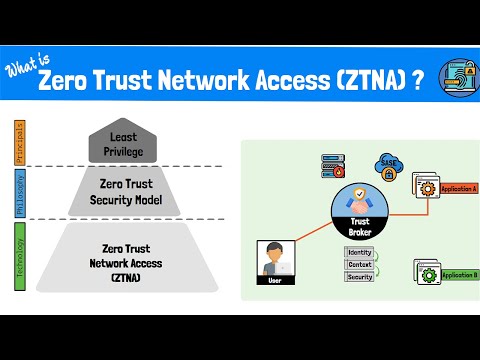
What is Zero Trust Network Access (ZTNA)? The Zero Trust Model, Framework and Technologies ExplainedПодробнее
Continuous Authentication for Zero Trust | NetIQПодробнее

Authorization for Zero TrustПодробнее

Adaptive Access in a Zero Trust World | NetIQПодробнее

Why does your Zero Trust Setup need adaptive Multi-Factor Authentication?Подробнее

Achieving MFA With FortiToken Cloud | Zero Trust Network AccessПодробнее

Zero Trust Authentication DefinedПодробнее

Cybersecurity and Zero TrustПодробнее

Difference Between Zero Trust Network Access and Zero Trust Application AccessПодробнее

Akamai Enterprise Application Access: Zero Trust Network AccessПодробнее

Zero Trust Security with SilverfortПодробнее
Duo Security: Cloud Based Zero Trust SecurityПодробнее
Zero-Trust - Secure Remote Worker: (Part3) Zero Trust Network Access: VPN-less to Private Web ServerПодробнее

STOP using this Two-Factor Authentication (2FA) method!Подробнее
PeopleSoft Multi-Factor (MFA) Integration: Data Security & User Experience | Zero TrustПодробнее

Webinar: How to Secure Your Infrastructure in a Zero Trust WorldПодробнее

5 Tips About Zero Trust Network AccessПодробнее
